Role Based Access Controls (RBAC)
This article gives an overview of Role Based Access Controls.
![]() Estimated Read Time: 5 minutes
Estimated Read Time: 5 minutes
Sections in this article:
Note: Access to the features in this article will depend on your user permissions and the configuration of your tenant.
What Are Role Based Access Controls (RBAC)?
Role Based Access Controls (RBAC) allow user access to be managed at the group level rather than individually, ensuring a structured and efficient approach to permissions.
In Gatekeeper, the primary object is the contract record, as all other objects link back to it. Using any combination of these objects, you can provide the correct level of access for your users.
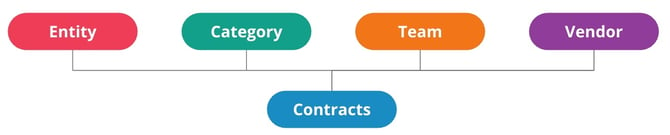
When setting up RBAC groups, there are three key objects to consider:
- Entities – The legal entities that make up your organisation that are parties to contracts.
- Teams – Typically aligned with departments, e.g. Legal or InfoSec.
- Categories – Used to group contracts, describing the goods or services obtained under the contract.
Additionally, you can provide access to specific contracts and vendors for access groups.
Note: Your teams, categories, or entities may have been renamed within your tenant, but this article will reference their default names.
Benefits of RBAC:
- Ensures users have only the necessary access, enhancing security and control.
- Allows system administrators to efficiently manage user access at scale through access groups.
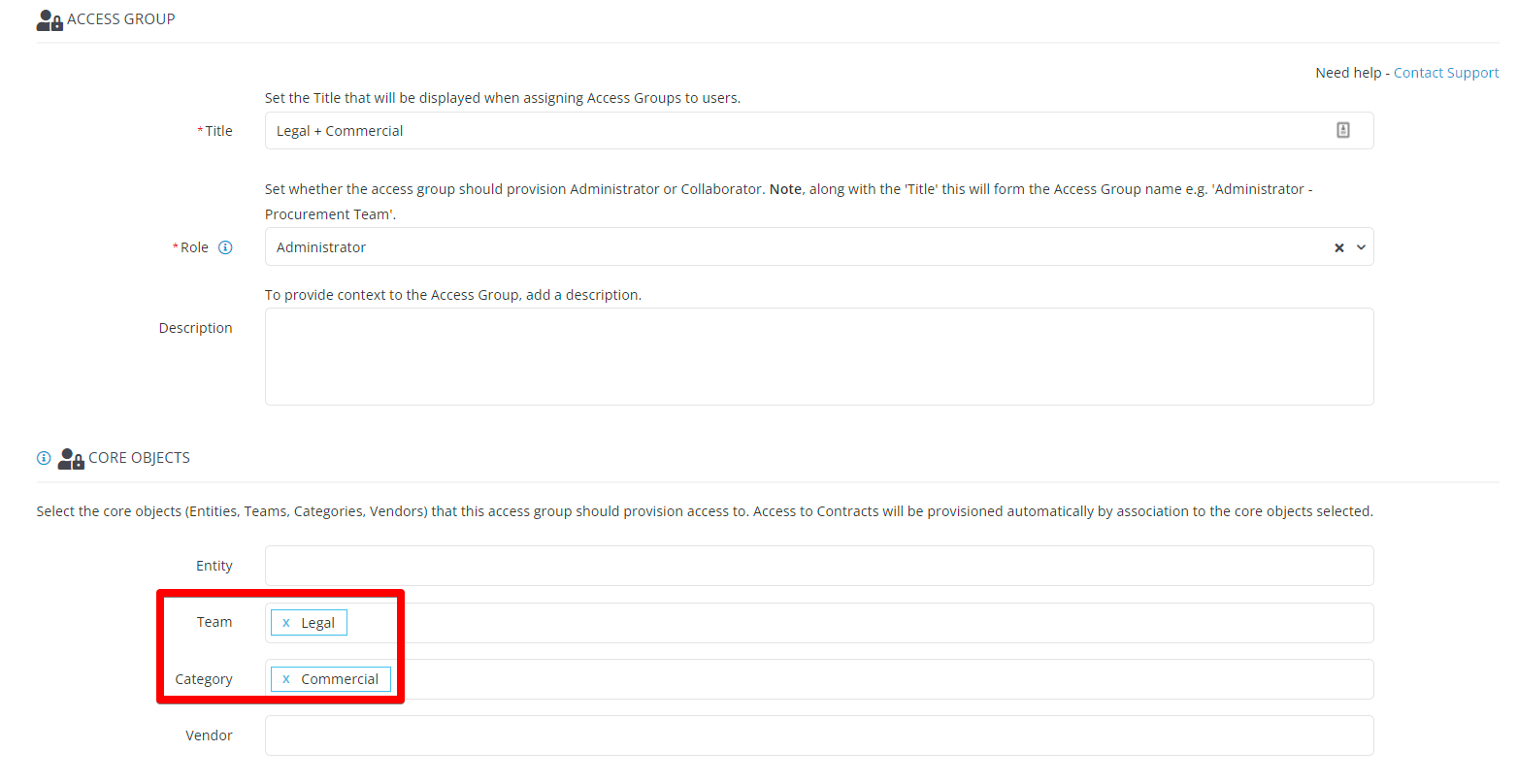
Example
John is part of the Legal team and manages only Commercial contracts. Using RBAC, you can create an access group where Team = Legal and Category = Commercial, ensuring John can view all relevant contracts and vendors.
Boolean Operators
When setting up RBAC Groups, it's important to understand how the And vs. Or operator affects access:
And Operator
A record must meet all selected conditions for the user to access it.
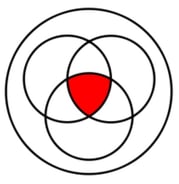
In the Venn diagram, each circle represents a different core object provisioned in an RBAC group, such as entity, team, or category. The red-shaded intersection represents contracts that meet all conditions:
✅ The contract is linked to the entity
✅ AND linked to the team
✅ AND linked to the category
Only contracts that meet all conditions will be accessible. The AND operator is more restrictive, as fewer records meet all conditions.
For example, if a group is set to Team = Legal AND Category = Commercial, users can only access contracts that belong to the Legal team and are categorised as Commercial.
Access groups may also provision core objects through secondary associations. These occur when a provisioned contract is linked to additional core objects not explicitly selected in the group. In such cases, users receive Collaborator access to these indirectly associated objects. Expand the following section for a detailed breakdown of what users can do:
Permissions Matrix: And Operator
| Viewing Object | Adding Object | Editing Object | Deleting Object | Linking a Contract to an Object | |
|---|---|---|---|---|---|
| Entities | ⚠️ A user can view the entities provisioned to them. | ❌ A user can't add entities. | ⚠️ A user can only edit the entities provisioned to them. | ❌ A user can't delete an entity. However, once all contracts linked to a given entity are deleted, the entity will no longer be accessible. | ⚠️ When adding a contract and linking it to an entity, the entity drop-down will only list entities provisioned to them. |
| Teams | ⚠️ A user can view the teams provisioned to them. | ⚠️ A user can add teams, but only 'in-line' while adding a contract record. | ⚠️ A user can only edit the teams provisioned to them. | ❌ A user can't delete a team. However, once all contracts linked to a given team are deleted, the team will no longer be accessible. | ✅ When adding a contract and linking it to a team, the team drop-down will list all teams. |
| Categories | ⚠️ A user can view the categories provisioned to them. | ⚠️ A user can add categories, but only 'in-line' while adding a contract record. | ⚠️ A user can only edit the categories provisioned to them. | ❌ A user can't delete a category. However, once all contracts linked to a given category are deleted, the category will no longer be accessible. | ✅ When adding a contract and linking it to a category, the category drop-down will list all categories. |
| Vendors | ⚠️ A user can view the vendors provisioned to them. | ⚠️ A user can add vendors, but only 'in-line' while adding a contract record. | ⚠️ A user can only edit the vendors provisioned to them. | ❌ A user can't delete a vendor. However, once all contracts linked to a given vendor are deleted, the vendor will no longer be accessible. | ✅ When adding a contract and linking it to a vendor, the vendor drop-down will list all vendors. |
| Contracts | ⚠️ A user can only view contracts which are linked to the entities and teams and categories and vendors provisioned to them. | ✅ A user can add contracts. | ⚠️ A user can only edit the contracts provisioned to them. | ⚠️ A user can only delete the contracts provisioned to them. | ⚠️ A user can create contracts, linking them to objects is restricted as detailed above. |
Or Operator
A record only needs to meet one of the selected conditions for the user to gain access to it.
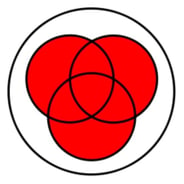
In this Venn diagram, the red area highlights the contracts that will be accessible based on any of these associations:
- All contracts linked to the entity
- OR all contracts linked to the team
- OR all contracts linked to the category
This makes the OR operator less restrictive than the AND operator, as adding more objects to an access group will provision more contracts by association.
For example, if a group is set to Team = Legal OR Category = Commercial, users in this group will have access to all contracts in the Commercial category, even if they aren’t linked to the Legal team.
Access groups may also provision core objects through secondary associations. These occur when a provisioned contract is linked to additional core objects not explicitly selected in the group. In such cases, users receive Collaborator access to these indirectly associated objects.
Expand the following section for a detailed breakdown of what users can do:
Permissions Matrix: Or Operator
| Viewing Object | Adding Object | Editing Object | Deleting Object | Linking a Contract to an Object | |
|---|---|---|---|---|---|
| Entities | ⚠️ A user can view the entities provisioned to them. In addition, a user can view the entities which are linked to contracts, which in turn are linked to the categories, teams or vendors provisioned to them. |
❌ A user can't add entities. | ⚠️ A user can only edit the entities provisioned to them as administrator. A user can't edit the additional entities they are able to view. |
❌ A user can't delete an entity. However, once all contracts linked to a given entity are deleted, the entity will no longer be accessible. | ⚠️ When adding a contract and linking it to an entity, the entity drop-down will only list entities which are linked to contracts already linked to the entities provisioned to them as administrator. |
| Teams | ⚠️ A user can view the teams provisioned to them. In addition, a user can view the teams which are linked to contracts, which in turn are linked to the entities, categories or vendors provisioned to them. |
⚠️ A user can add teams, but only 'in-line' while adding a contract record. | ⚠️ A user can only edit the teams provisioned to them as administrator. A user can't edit the additional teams they are able to view. |
❌ A user can't delete a team. However, once all contracts linked to a given team are deleted, the team will no longer be accessible. | ✅ When adding a contract and linking it to a team, the team drop-down will list all teams. |
| Categories | ⚠️ A user can view the categories provisioned to them. In addition, a user can view the categories which are linked to contracts, which in turn are linked to the entities, teams or vendors provisioned to them. |
⚠️ A user can add categories, but only 'in-line' while adding a contract record. | ⚠️ A user can only edit the categories provisioned to them as administrator. A user can't edit the additional categories they are able to view. |
❌ A user can't delete a category. However, once all contracts linked to a given category are deleted, the category will no longer be accessible. | ✅ When adding a contract and linking it to a category, the category drop-down will list all categories. |
| Vendors | ⚠️ A user can view the vendors provisioned to them. In addition, a user can view the vendors which are linked to contracts, which in turn are linked to the entities, categories or teams provisioned to them. |
⚠️ A user can add vendors, but only 'in-line' while adding a contract record. | ⚠️ A user can only edit the vendors provisioned to them as administrator. A user can't edit the additional vendors they are able to view. |
❌ A user can't delete a vendor. However, once all contracts linked to a given vendor are deleted, the vendor will no longer be accessible. | ✅ When adding a contract and linking it to a vendor, the vendor drop-down will list all vendors. |
| Contracts | ⚠️ A user can only view contracts which are linked to the entities, teams, categories or vendors provisioned to them. | ✅ A user can add contracts. | ⚠️ A user can only edit contracts which are linked to the entities, teams, categories or vendors provisioned to them as administrator. | ⚠️ A user can only delete contracts which are linked to the entities, teams, categories or vendors provisioned to them as administrator. | ⚠️ A user can create contracts, linking them to objects is restricted as detailed above. |
Set the Boolean Operator
Note: This is a global setting, so will dictate all RBAC Groups.
To set the Boolean Operator:
- From the navigation menu, expand the Settings option, then click Configuration.
- Click Role Based Access Control (RBAC) Configuration.
- Select the appropriate radio button.
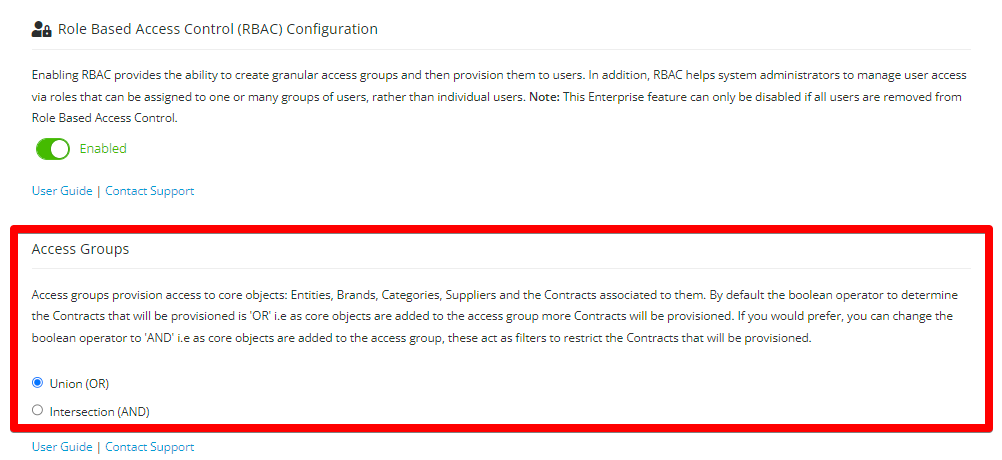
- Click Save.
Additional Reading
- Create an Access Group - this article walks through the steps for creating an access group.